Chapter 4 Using Crypto-C 133
Using Cryptographic Hardware
the application has been compiled.
If more than one hardware method is present for the same AM — for example, if the
application includes hardware methods implementing RSA encryption from two
different manufacturers —
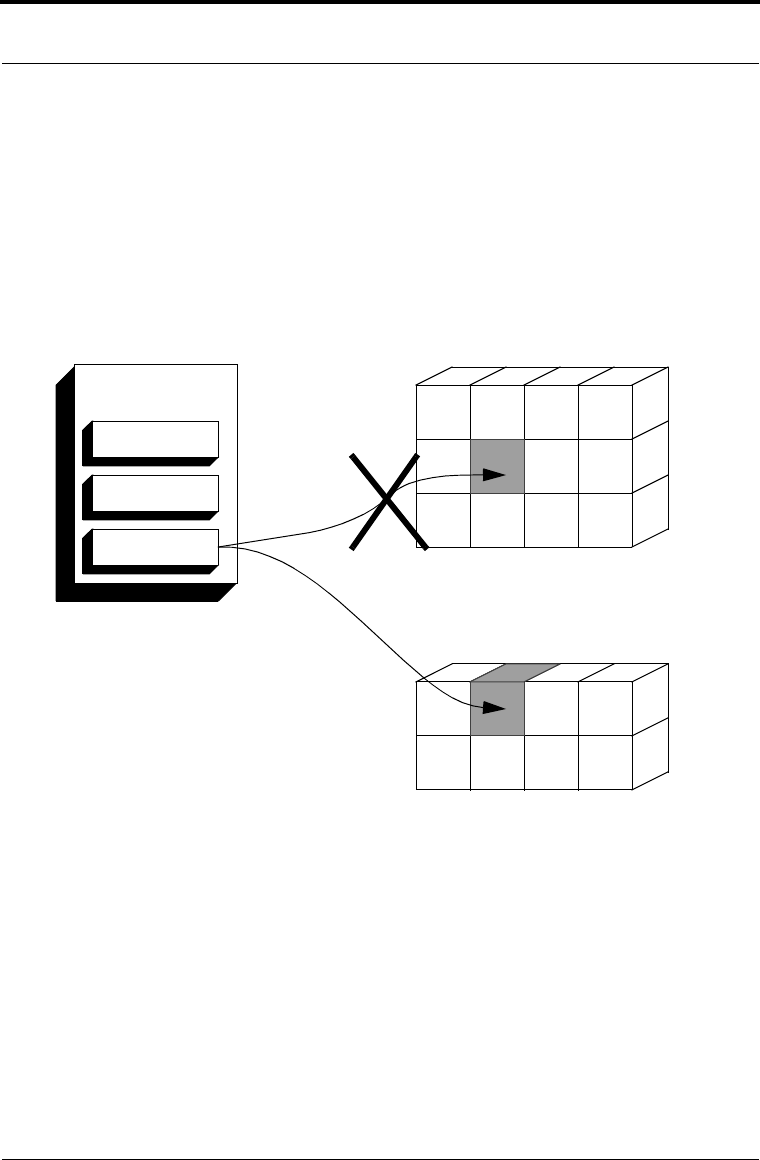
B_CreateSessionChooser includes all available hardware
methods. When an object’s methods are instantiated at initialization, Crypto-C loads
the object with the first compatible method from the session chooser. Figure 4-2
shows how an algorithm object operates with a hardware interface.
Figure 4-2 Algorithm Object in a Hardware Implementation
During the call to
B_CreateSessionChooser, Crypto-C tests for the presence of the
hardware; if hardware is present, the hardware method is included in the session
chooser. If no hardware is present, then the application defaults to the Crypto-C
software AM or to a software emulation if one is included in the chooser.
To extend the functionality of the BHAPI interface to include key-token operations,
Crypto-C supplies some AIs that are only available when
B_CreateSessionchooser is
used. These AIs have software-emulated versions, but can only be accessed via
inclusion in the hardware chooser.
Functions
Algorithm Object
Type (AI)
Parameters
BSAFE Software Library
Hardware Methods
