Cryptography Overview
50 RSA BSAFE Crypto-C Developer’s Guide
Normally, the mixing is a message digest. This makes the task of getting from
password to key very time-consuming for an attacker. Digesting a password with a
salt helps thwart dictionary attacks. An attacker could put together a “dictionary” of
keys generated from likely passwords, and try out each key on encrypted data. This
would greatly reduce the amount of work necessary to find the key and may make it
feasible to recover encrypted material. With a salt, the attacker would have to create a
dictionary of keys generated from each password, but each password would then
have to have a dictionary of each possible salt.
Crypto-C uses the methods described in PKCS v1.5 to implement password-based
encryption. The methods use a message digest algorithm with a specific means of
padding to increase the search space for dictionary attacks against the key. The
applicable Algorithm Information Types (AIs) are: AI_MD2WithDES_*,
AI_MD2WithRC2_*, AI_MD5WithDES_*, AI_MD5WithRC2_*, and
AI_SHA1WithDES_*.
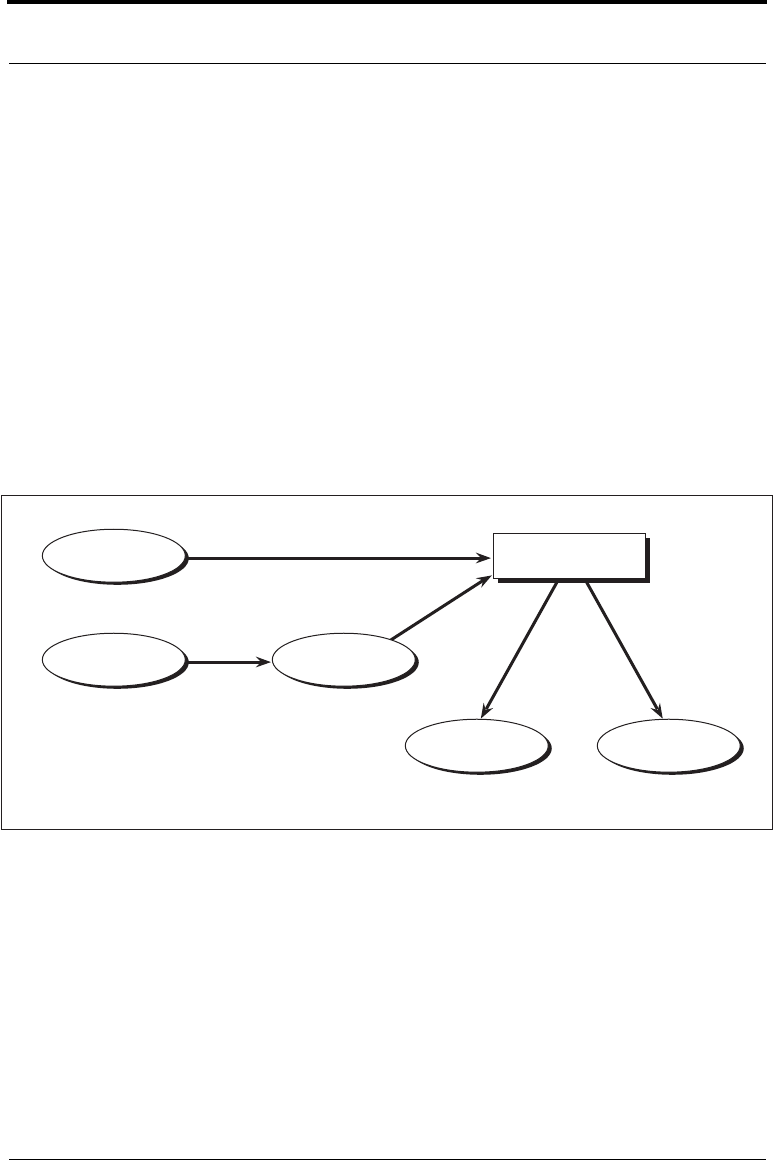
Figure 3-8 DES Key and IV Generation for Password Based Encryption
Public-Key Cryptography
In 1976, Stanford graduate student Whitfield Diffie and Stanford professor Martin
Hellman invented public-key cryptography. In this system, each person owns a pair of
keys, called the public key and the private key. The owner of each key pair publishes
the public key and keeps the private key secret.
Suppose Alice wants to send a message to Bob. She finds his public key and encrypts
Password
Message digest
Pseudo-random
bytes
Salt
Key
8 bytes
I V
8 bytes
