Getting Started with ETPM
140 EncrypTight User Guide
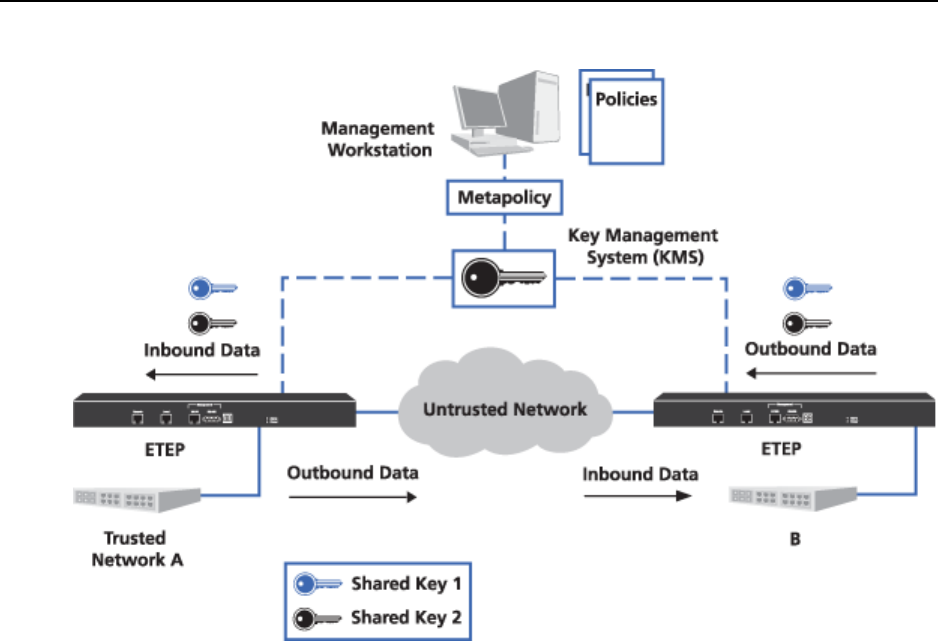
Figure 48 Key generation with one ETKMS
In this scenario, you could use either a local ETKMS or an external ETKMS. The ETKMS generates and
sends the same shared key to the PEP encrypting the outbound data and the PEP decrypting the inbound
data. Each PEP needs a unique key to encrypt outbound data, and in turn this key must be shared with the
PEP’s peers.
● In Figure 48, the ETKMS generates Shared Key 1 and distributes this key to PEP B to encrypt the
outbound data and to PEP A to decrypt the inbound data.
● The ETKMS also generates Shared Key 2 and distributes this key to PEP A to encrypt the outbound
data from Network A and to PEP B to decrypt the inbound data to Network B.
A policy can use two or more PEPs that are controlled by different ETKMSs. In this case, first the
controlling ETKMSs exchange the keys PEPs need for decrypting traffic and then they send the
appropriate keys to the PEPs they control. Figure 49 illustrates key generation and distribution when
different ETKMSs control the PEPs required to enforce an encryption policy. This scenario would most
likely involve two external ETKMSs.