Advanced Uses for Networks in Policies
EncrypTight User Guide 163
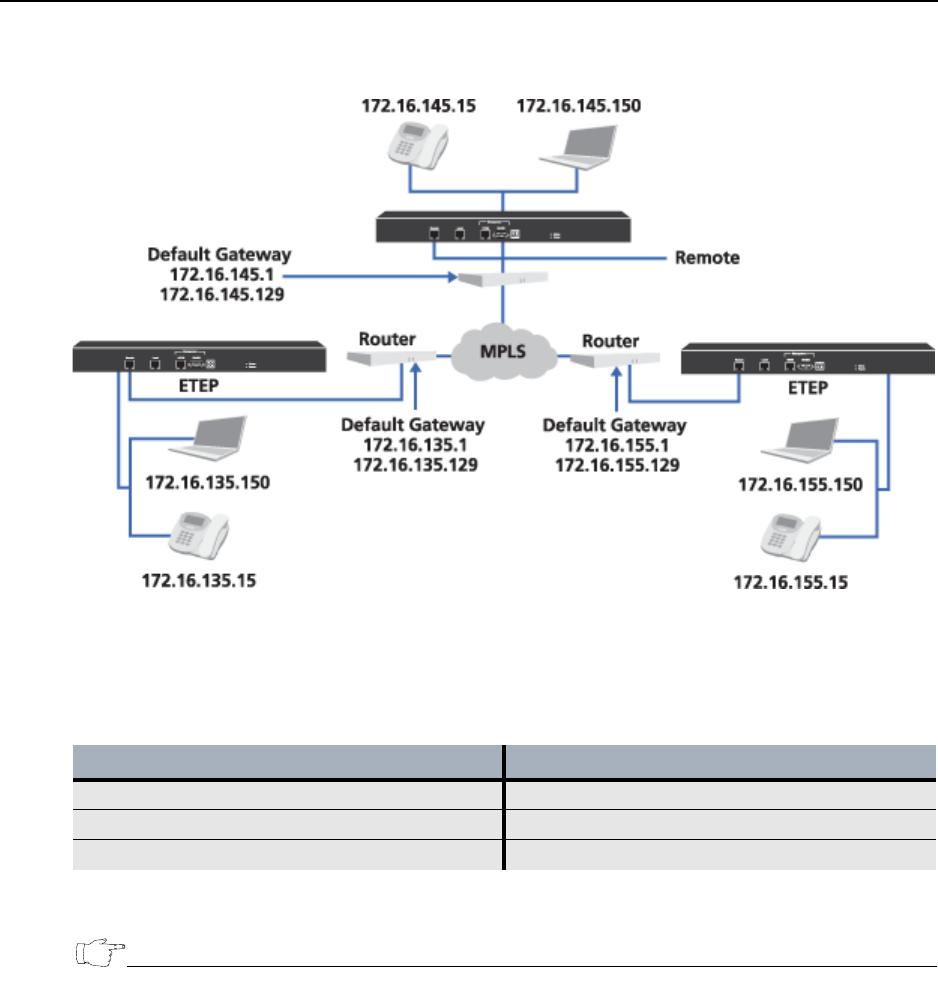
Figure 57 Networks with non-contiguous network masks are used in a bypass policy
that encompasses all the x.x.x.1 and x.x.x.129 addresses
Defining networks with non-contiguous masks allows you to create a single bypass policy that
encompasses all the .1 and .129 addresses, enabling the local sites on the 172.16.x.x network to manage
the devices on the remote port side of the PEP. By defining the networks as shown in Table 42, you
eliminate the need to create individual bypass policies for each subnet in the network.
NOTE
When you use non-contiguous network masks, the network set must include a PEP that supports the
feature (ETEP v.1.4 and later). In addition, all network sets in a policy must include supporting PEPs.
ETPM prevents you from dragging non-supporting elements into a network set or policy when non-
contiguous networks masks are in use.
Table 42 Networks definitions
IP Address Network Mask
0.0.0.129 (laptops) 0.0.0.255
0.0.0.1 (VoIP phones) 0.0.0.255
172.16.0.0 (any traffic on this network) 255.255.0.0