Policy Deployment
EncrypTight User Guide 207
You create Layer 4 policies using ETEPs that are configured to operate as Layer 3 PEPs. Create the
networks, network sets, and policies as you would for Layer 3 IP policies. In the policy editor, select the
option to preserve the address, protocol, and port. This option encrypts only the payload data, making the
policy a Layer 4 policy.
Layer 4 IP encryption policies use AES-256 for encryption and HMAC-SHA-1 for authentication. The
ETEP PEPs do not support 3DES or HMAC-MD5 at Layer 4.
To create a new Layer 4 policy:
1 Right click anywhere in the policy view and select an IP policy type from the shortcut menu.
2 Follow the instructions for creating the type of policy you selected as discussed in “Adding Layer 3
IP Policies” on page 191.
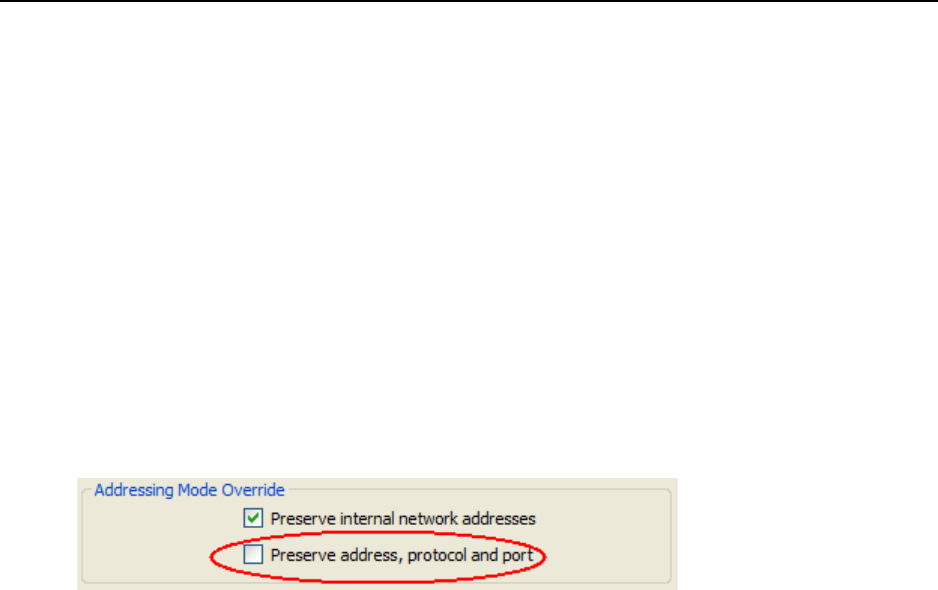
3 From the Addressing Mode Override section of the policy editor, select Preserve address, protocol
and port (see Figure 80).
4 Save the policy.
Figure 80 Option to Encrypt the Packet Payload Only
Policy Deployment
This section includes the following topics:
● “Verifying Policy Rules Before Deployment” on page 207
● “Deploying Policies” on page 208
● “Setting Deployment Confirmation Preferences” on page 208
Verifying Policy Rules Before Deployment
The Verify Policies tool checks your policies for conformance to the policy rules prior to deployment.
This tool performs the same consistency checks on policies that are performed during a deploy operation.
It differs from the deployment verification in that it does not check communication links to the ETKMS.
The Verify Policies tool checks for features that are not universally supported across PEP models and
software versions. It looks for inconsistencies such as using a mixture of Layer 2 and Layer 3 PEPs in a
policy, using contiguous and non-contiguous network masks in a network set, and the use of virtual IP
addresses.
Verifying policies prior to deployment is useful if you have done any of the following:
● Made edits to any policy element since you last deployed policies: PEPs, networks, network sets, or
policy definitions.
● The PEPs in a policy are running a mix of software versions, for example ETEPs running versions
1.4, 1.5, and 1.6.