Configuring the Certificate Policies Extension
EncrypTight User Guide 271
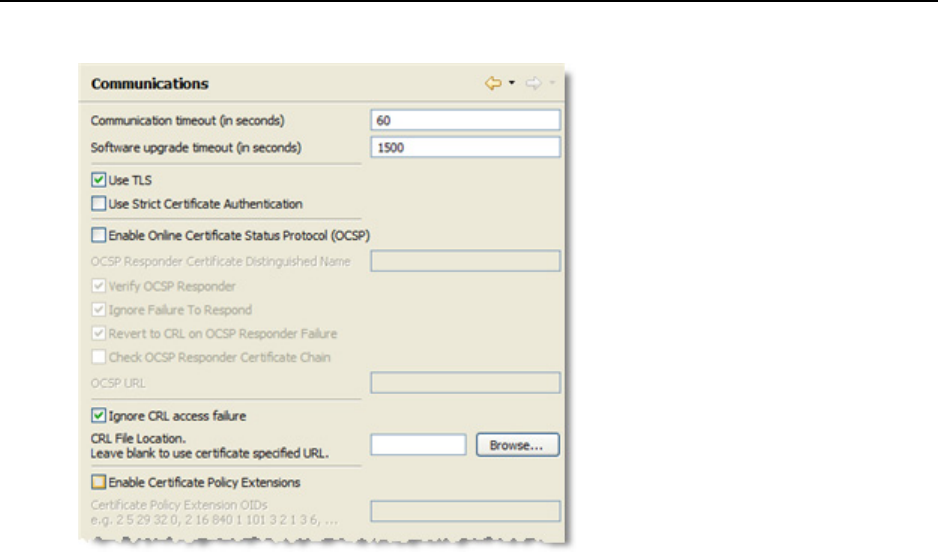
Figure 95 Communications Preferences
About the Policy Constraints Extension
The certificate policies extension can be used in conjunction with the policy constraint extension. This
extension is configured by your CA and requires no setup in EncrypTight components. It places
additional controls on how certificates can be used. The policy constraints extension can:
● Prohibit policy mapping
Policy mapping is the practice by which one OID is considered equivalent to a different OID. When
policy mapping is prohibited, a value in the extension indicates the number of additional certificates
in the chain that can be checked before policy mapping is prohibited. Beyond that point, policy
mapping is not allowed and authentication can fail.
● Require that every certificate in the certificate chain include acceptable policy identifiers, as specified
in the certificate policies extension
With this option, a value in the extension indicates the number of additional certificates in the chain
that can be checked before all certificates in the chain must include acceptable policy identifiers,
either an exact match to an OID configured in the device or an OID considered equivalent through
policy mapping. If the next certificate in the chain does not include acceptable OIDs, authentication
can fail.
Your CAs can provide information about their practice for using these extensions.
Related topics:
● “Working with Certificates for EncrypTight and the ETKMSs” on page 272
● “Working with Certificates and an HSM” on page 275
● “Working with Certificates for the ETEPs” on page 277
● “Enabling and Disabling Strict Authentication” on page 292


















