Creating a Policy: An Overview
EncrypTight User Guide 141
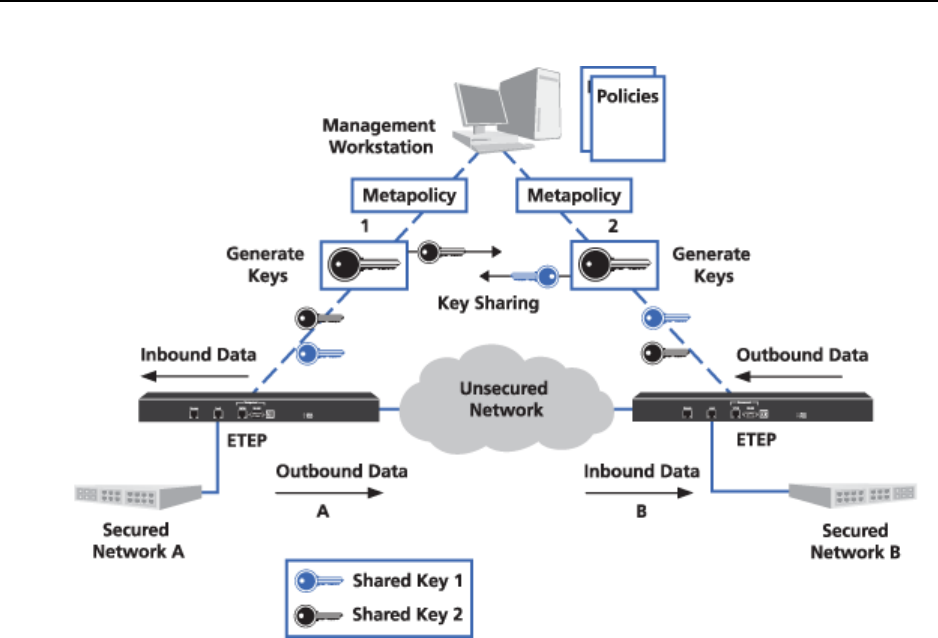
Figure 49 Key generation with multiple ETKMSs
The ETKMS generating the key for a PEP’s outbound data shares the key with the ETKMSs that control
the PEPs that decrypt the data. In Figure 49, ETKMS 1 controls PEP A and is responsible for generating
Shared Key 2. ETKMS 2 controls PEP B and is responsible for generating Shared Key 1.
● Shared Key 2 is used to encrypt the outbound data in PEP A and it is used by PEP B to decrypt the
data received from Network A. ETKMS 1 shares Shared Key 2 with ETKMS 2, which distributes the
key to PEP B.
● Shared Key 1 is used to encrypt the outbound data from PEP B and it is used by PEP A to decrypt the
data received from Network B. ETKMS 2 shares Shared Key 1 with ETKMS 1, which distributes the
key to PEP A.
Creating a Policy: An Overview
The following steps summarize how to create a point-to-point IP policy, using the example in Figure 50.
If you are configuring a policy for a Layer 2 Ethernet network the overall procedure is the same but the
specific components are different.