Distributed Key Topologies
EncrypTight User Guide 21
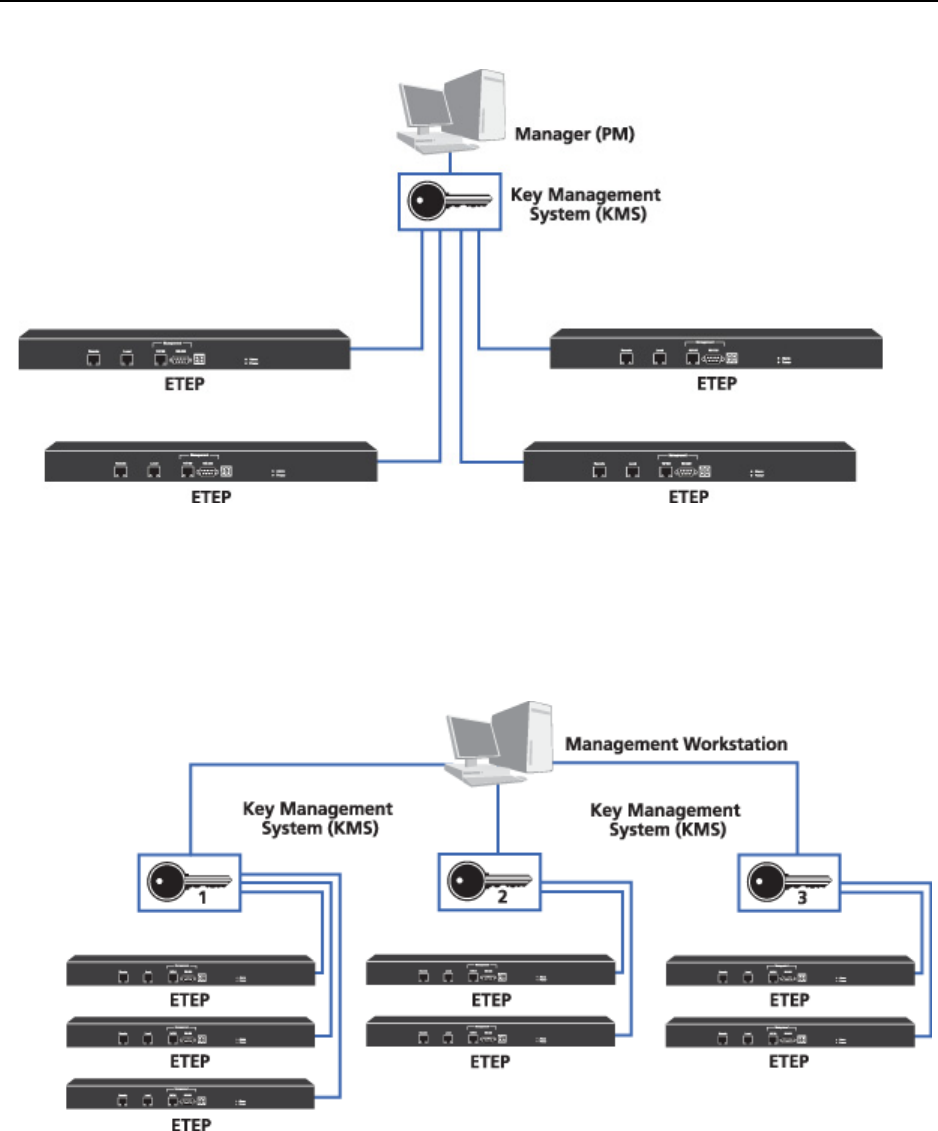
Figure 3 Single ETKMS for multiple sites
Figure 4 illustrates an EncrypTight deployment using multiple ETKMSs. With large, complex networks
that have hundreds of PEPs, you might want to use multiple ETKMSs. Each ETKMS distributes keys for
the PEPs it controls. For example: ETKMS 1 distributes the policies and keys to PEPs A, B, and C.
ETKMS 2 distributes the policies and keys to PEPs D and E. ETKMS 3 distributes the policies and keys
to PEPs F and G.
Figure 4 Multiple ETKMSs in a network
Policy Enforcement Point
EncrypTight enforcement points (ETEPs) are encryption appliances that provide policy enforcement
functions, and are referred to generically as PEPs (policy enforcement points). According to the policies
distributed by the ETKMSs, the PEPs can encrypt and decrypt traffic, send traffic in the clear, or drop
traffic. Each PEP can be used in multiple policies simultaneously.


















