Getting Started with ETPM
142 EncrypTight User Guide
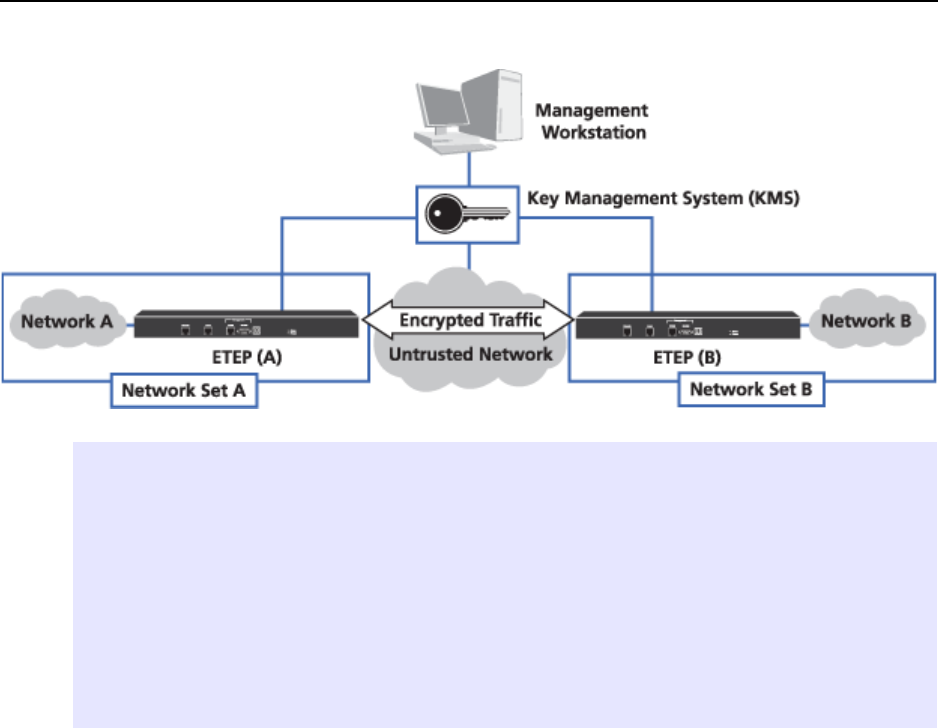
Figure 50 Sample point-to-point IP policy
Figure 50 illustrates an EncrypTight deployment with two networks. This example demonstrates how to
create a point-to-point policy to encrypt the traffic sent between the two networks over the untrusted
network.
To create a policy, the general steps are:
1 In the ETEMS Appliance Manager,
a Add and configure the PEPs you want to use.
b Push the configurations to the PEPs.
c Add and configure the ETKMSs you want to use.
2In ETPM,
a Add the networks you need.
b Create the network sets.
c Create the policies.
d Deploy the policies.
Elements of Figure 50:
1) ETKMS 1, IP address 192.168.1.33
A, B) PEP A, IP address 192.168.11.69
PEP B, IP address 192.168.11.224
Network A IP address 192.168.144.0
Network B IP address 192.168.154.0
Network Set A Includes Network A and PEP A, using ETKMS 1
Network Set B Includes Network B and PEP B, using ETKMS 1