EncrypTight Overview
18 EncrypTight User Guide
multiple Policy Enforcement Points (PEPs) can use common keys, while a centralized platform assumes
the function of renewing keys at pre-determined intervals.
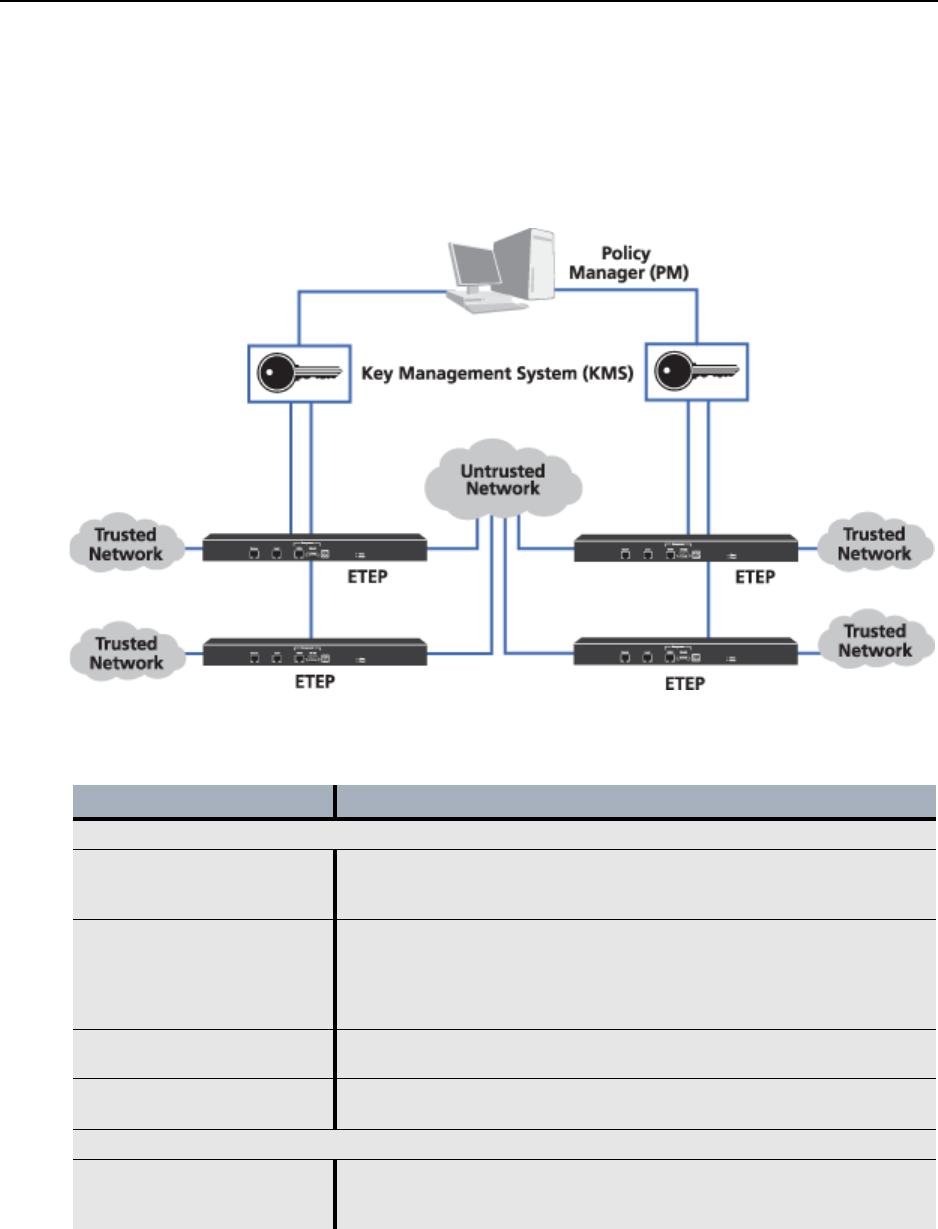
In this system, you use ETEMS to configure the PEPs, Policy Manager (ETPM) to create and manage
policies, and Key Management System (ETKMS) to generate keys and distribute keys and policies to the
appropriate PEPs. The PEPs encrypt traffic according to the policies and keys that they receive.
Figure 1 EncrypTight components
Using EncrypTight, you can create distributed key policies for the network topologies shown in Table 1.
Table 1 Network topologies
Topology Description
Layer 3 IP topologies
Hub and Spoke In a hub and spoke network, a hub network communicates with the
spoke networks and the spoke networks communicate only with the
hub network.
Multicast In multicast transmission, one or more networks send unidirectional
streams to a multicast network address. The multicast routers detect
the multicast transmission, determine which nodes have joined the
multicast network as destination networks, and duplicate the packet as
needed to reach all multicast destination networks.
Point-to-point In a point-to-point network, one network sends and receives data to
and from one other network.
Mesh In a mesh network, any network can send or receive data from any
other network.
Layer 2 Ethernet topologies
Mesh For Ethernet, you can create policies for mesh networks. Note that if
the network uses VLAN ID tags, you can also create policies for virtual
point-to-point connections.


















