Creating Distributed Key Policies
186 EncrypTight User Guide
1 Create a policy to encrypt all data to and from all networks. Assign this policy a relatively low
priority to ensure that any missed data will at least pass encrypted.
2 Design a pass in the clear policy and a drop policy with a higher priorities.
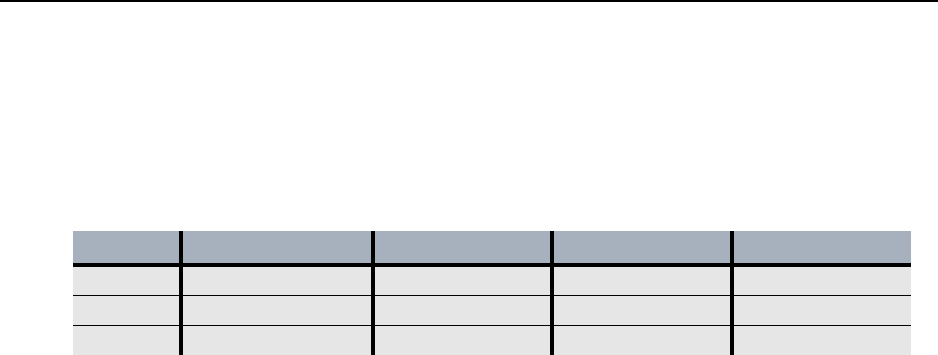
Table 46 illustrates policies for a mesh network that will pass Protocol 17 (UDP) traffic in the clear, drop
all protocol 55 (IP mobile) traffic, and encrypt all other traffic.
In this case, we started with the assumption that our main job was to encrypt traffic and then decide
which traffic to drop or pass in the clear. The PEP analyzes each packet starting with the highest priority
policy.
The alternative is to decide which traffic should be encrypted, which traffic should be passed in the clear,
and which traffic should be dropped. With this approach, you risk creating more policies to manage than
you need and increasing the management traffic on the network. You could also easily miss encrypting
important traffic.
Policy Size and ETEP Operational Limits
Various combinations of factors can reach or exceed the operational limits of the ETEP PEP, including
memory, processor speed, and the size of the policy file. Another core issue is the number of security
associations (SAs) a PEP can support.
An SA identifies what traffic to act on, what kind of security to apply, and the device with which the
traffic is being exchanged. SAs typically exist in pairs, one for each direction (inbound and outbound).
The policies deployed from ETPM create SAs between the PEPs. A simple point-to-point policy creates
two SAs on each PEP. More complex configurations such as a mesh policy create more SAs.
The policy file is an XML file sent to each PEP that identifies the type of policy, the ETKMSs used, the
policy lifetime, and the kind of traffic the policy affects. It also identifies the networks to be protected
and the PEPs to be used.
The size of a policy file is determined by the type of policy, the number of PEPs, and the number of
networks protected. On the ET0010A, the maximum size for the policy file is 512 KB. For the ET0100A,
the maximum size is 1024 KB.
If the policy file is larger than the maximum size, the rekey processing time on the PEP can exceed the
system timeout parameters. For example, with the ET0010A the rekey processing time for a 512 KB
policy file is approximately three minutes. If the rekey processing takes longer than this, timeouts and
errors occur that severely affect overall system performance. When timeouts and errors occur, keys can
expire or a policy might not actually be deployed.
To prevent this from happening, ETEP PEPs generate error messages and reject policy files that are larger
than the maximum size. The error messages are recorded in the ETKMS log file. For information about
viewing the ETKMS log file, see “ETKMS Log Files” on page 241.
Table 46 Encrypt all policy with exceptions
Policy Policy Type Priority Action Protocol Covered
1 Mesh 100 Encrypt All
2 Mesh 200 Drop 55
3 Mesh 300 Pass in Clear 17