ETEP Configuration
336 EncrypTight User Guide
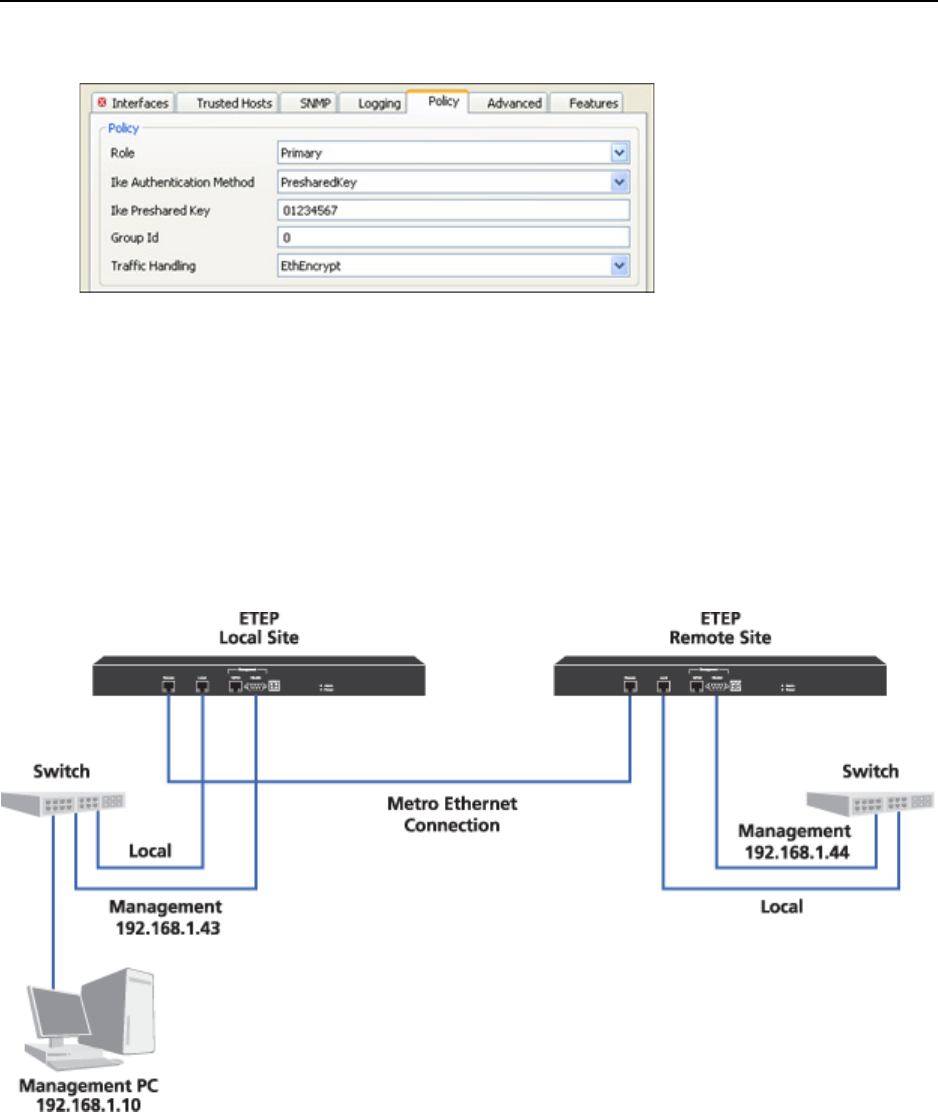
Figure 115 ETEP Policy tab
When ETEPs are first installed they pass all traffic in the clear until they receive policies. After you push
the Layer 2 point-to-point policy configuration to the ETEPs they will begin negotiations to encrypt
traffic. You can change the way in which the ETEP processes traffic by modifying the traffic handling
setting to pass traffic in the clear, discard traffic, or encrypt traffic.
If you are managing the ETEPs in-line as shown in Figure 116, the order in which you push
configurations to the ETEPs is important. The local ETEP (#2 in Figure 116) must be passing traffic in
the clear in order to push a configuration to the remote ETEP (#3 Figure 116). To maintain connectivity
with the remote ETEP’s management port, push the configuration to the remote ETEP first and then push
the configuration to the local ETEP.
Figure 116 Point-to-point Layer 2 Ethernet link
Note the following operational constraints and recommendations:
● Layer 2 point-to-point IKE policies are incompatible with local site manual key policies that are
created from the command line.
● When the ETEP is configured for Layer 2 point-to-point operation, the management port IKE server
is shut down, which prevents IKE SAs from being negotiated on the management port. If you plan to


















