Policy Design Examples
214 EncrypTight User Guide
To create the policies:
1 In ETEMS, add and configure the ETEPs to operate as Layer 2 PEPs.
2 Add the ETKMS for the policies.
3 Push the configurations to the ETEPs.
4 In ETPM, add the VLAN ID tags.
5 Create the policies using the settings described in “Policy Details” on page 213.
6 Deploy the policies.
Complex Layer 3 Policy Example
In this example, we have sixteen networks connecting to each other through a public WAN. Four of these
networks are considered regional centers. Each regional center has three branches.
Figure 84 Network example
The requirements for our policies are as follows:
● “Encrypt Traffic Between Regional Centers” on page 214
● “Encrypt Traffic Between Regional Centers and Branches” on page 215
● “Passing Routing Protocols” on page 218
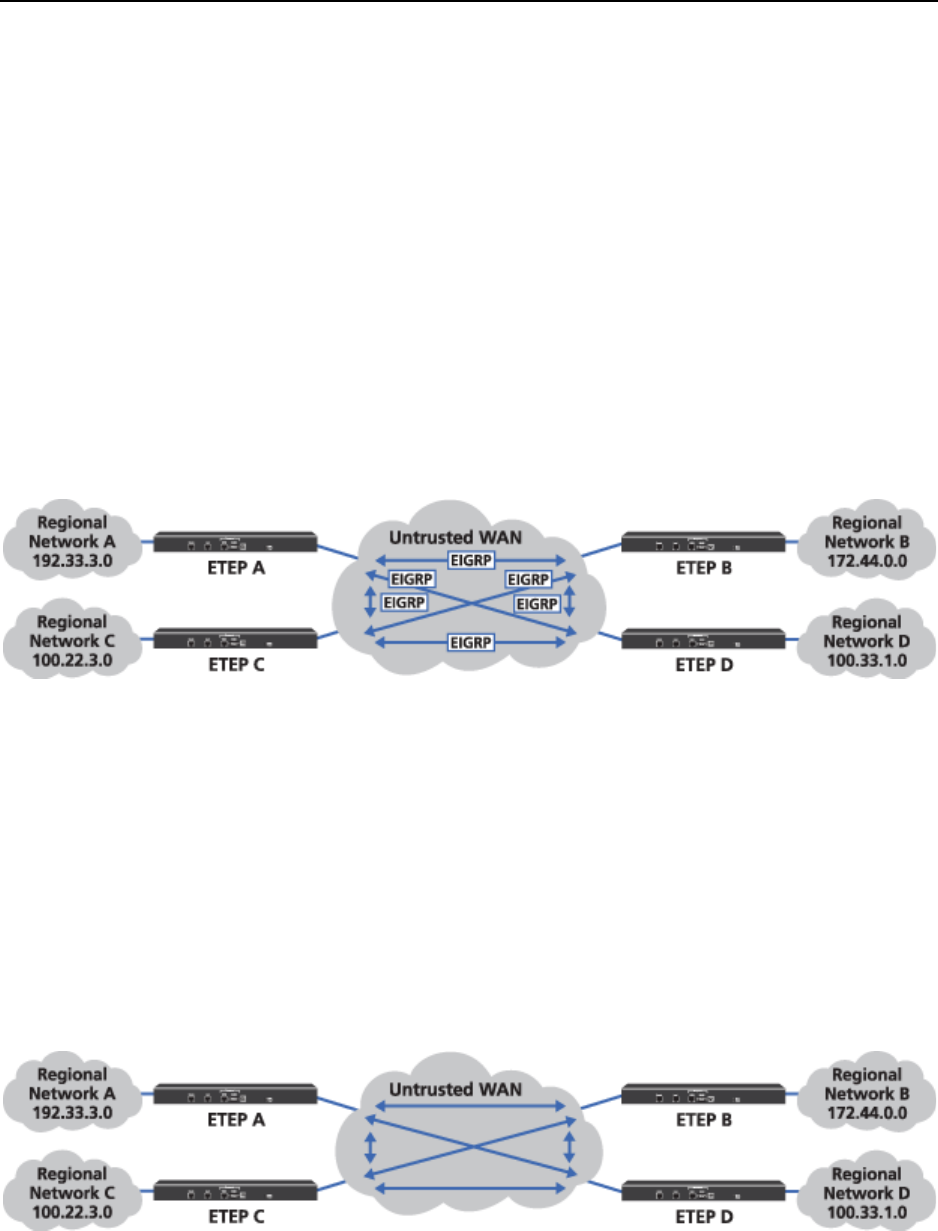
Encrypt Traffic Between Regional Centers
In order to encrypt traffic between the four regional centers, create a Mesh IPSec policy with each
regional network in a different network set.
Figure 85 Regional mesh encryption policy