Working with Certificates for EncrypTight and the ETKMSs
EncrypTight User Guide 273
To generate a key pair:
1 From the command line, use the following command to generate a public/private key pair:
keytool -genkeypair -dname {“cn=<Entity Name>, ou=<Organizational Unit>,
o=<Organization>, c=<Country>”} -alias <alias> -keypass <key password>
-keystore <keystore> -keyalg <algorithm> -storepass <password>
-validity <n>
For example:
keytool -genkeypair -dname “cn=ETKMS3, ou=Storage o=MyCompany c=US”
-alias Cert1 -keypass password1 -keystore C:\Safe\mykeystore -keyalg RSA
-storepass password2 -validity=180
This would generate a keypair and self-signed certificate for the entity named “ETKMS3” in the
organizational unit of “Storage,” part of the organization “MyCompany,” in the United States. The alias
of the certificate is “Cert1” and it is valid for 180 days.
Requesting a Certificate
Using the keytool -certreq command, create a certificate request to be sent to your CA.
To create the certificate request:
1 From the command line, use the following command to generate a certificate request:
keytool -certreq -file <filename>
Where filename is the name of the certificate signing request. You must use the filename extension
of .csr.
2 When prompted, enter the keystore password.
3 Using the procedure require by your CA, send the CSR file to your CA.
For example:
keytool -certreq -file ETKMS3.csr
This creates a certificate request file names “ETKMS3.csr” that you can send to your CA.
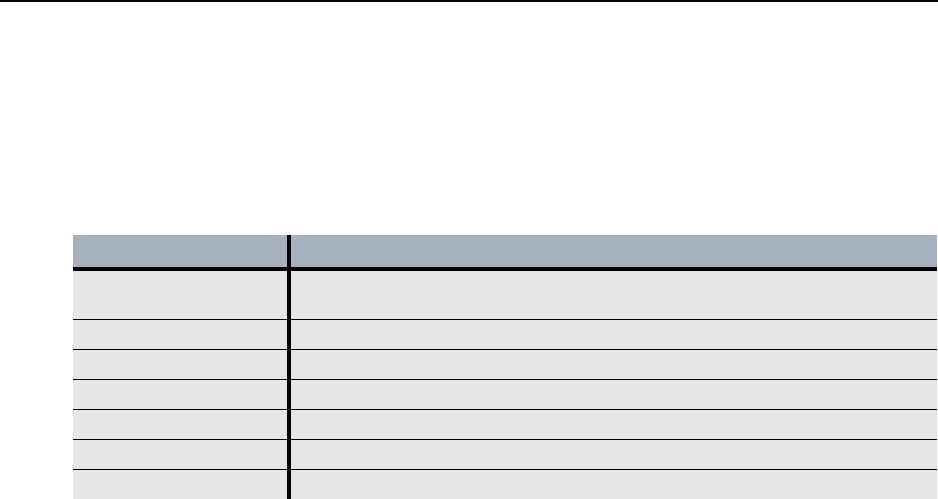
Table 70 Keytool genkeypair Command
Parameter Description
dname The distinguished name parameters for the certificate. For information about
this parameter, refer to “Certificate Information” on page 264.
alias The name of the keystore entry.
keypass The password for the private key.
keystore The name and location of the keystore.
keyalg The algorithm used to generate the keys.
storepass The password for the keystore.
validity The number of days for which the certificate entry is valid.


















