Advanced Uses for Networks in Policies
EncrypTight User Guide 161
clear.
ETPM accepts non-contiguous network masks, which allow you to create policies between particular
addresses in your network. For example, a network of 10.0.0.1 with a mask of 255.0.0.255 allows all
devices with an IP address of 10.x.x.1 to be managed by a particular policy. This feature is available only
with ETEP PEPs. See “Using Non-contiguous Network Masks” on page 162 for more information.
Advanced Uses for Networks in Policies
If you are familiar with network addressing and network masks, you can use subnetting to make your
policies more efficient.
● “Grouping Networks into Supernets” on page 161
Use supernetting to reduce the number of SAs and keys on each PEP in large deployments.
● “Using Non-contiguous Network Masks” on page 162
Use non-contiguous network masks to apply policies to a specific IP address scheme.
Grouping Networks into Supernets
Working with large networks, a considerable number of security associations (SAs) and keys can result
on each PEP. One way to avoid this is to look for subnetworks within each network set that have
contiguous addressing. You can combine these subnets to reduce the number of SAs and keys on each
PEP.
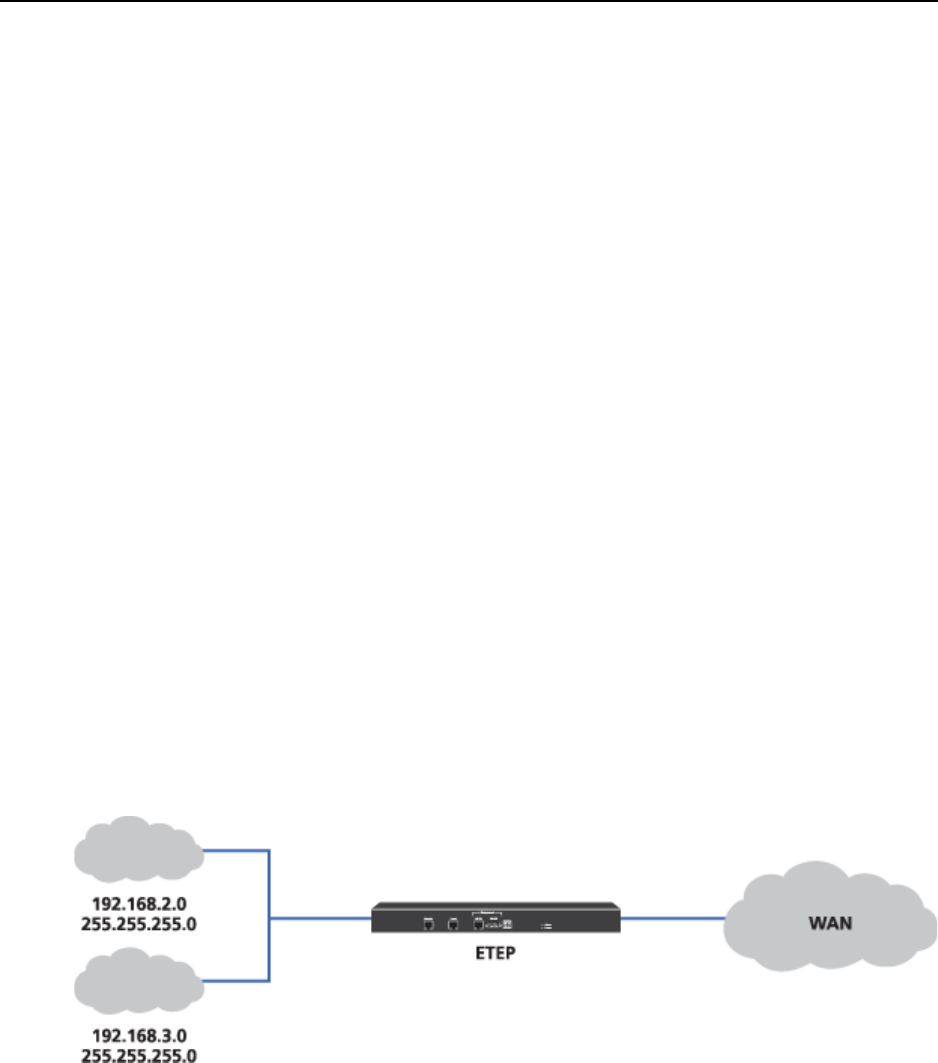
In Figure 55, if you set up each of these networks as a separate network in ETPM, and the policy
encrypts traffic between these two networks and five other networks, the PEP for this network set would
contain 10 SAs and keys for each direction.
Figure 55 Two networks with contiguous addressing
As illustrated in Figure 56, the two networks 192.168.2.0 with subnet mask 255.255.255.0 and
192.168.3.0 with subnet mask 255.255.255.0 could be grouped into one network 192.168.2.0 with subnet
mask 255.255.254.0.