Security within EncrypTight
EncrypTight User Guide 23
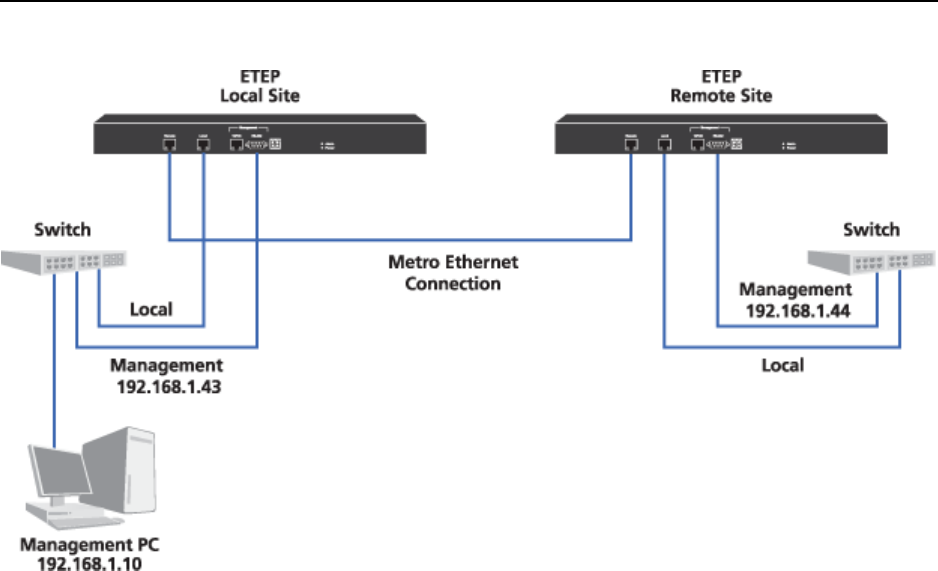
Figure 6 Layer 2 Point-to-Point Deployment
Use the Policy Manager (ETPM) and Key Management System (ETKMS) to create a Layer 3 point-to-
point distributed key policy as one of several policies in a larger, more complex EncrypTight deployment.
The ETEP’s variable speed feature is controlled by the installation of a license. Note that you cannot
install a license on the ETEP until you first enter a license for EncrypTight. For more information about
licensing, see “Managing Licenses” on page 56.
Related topics:
● “Distributed Key Topologies” on page 17
● “EncrypTight Element Management System” on page 20
● “Policy Manager” on page 20
● “Key Management System” on page 20
● “Policy Enforcement Point” on page 21
● “Creating Layer 2 Point-to-Point Policies” on page 335
Security within EncrypTight
Because EncrypTight generates keys that provide security throughout a network, it is critical that the
EncrypTight components also be secured.
Security in the EncrypTight system has two general areas:
● “Secure Communications Between Devices” on page 24
● “Secure Key Storage within the ETKMS” on page 24


















