Creating Distributed Key Policies
196 EncrypTight User Guide
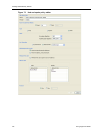
Table 49 Mesh policy entries
Field Description
Name Enter a unique name to identify the policy. Names can be 1 - 40 characters in
length. Alphanumeric characters and spaces are valid. The special characters
<, >, &, “ *, ?, /, \, : and | cannot be used in the policy name. Names are not
case sensitive.
Priority Enter the priority for this policy from 1 to 65000. PEPs enforce policies in
descending priority order with the highest priority number processed first.
Renew Keys/
Refresh
Lifetime
Specifies the lifetime of the keys and policies, and the frequency at which the
keys are regenerated and policies’ lifetimes are updated on the PEPs.
Regenerate keys and update policies either at a specified interval in hours or
daily at a specified time. Click either Hours or Daily.
•Hours - enter the re-key interval in hours between 0 and 65535 hours. 0
hours causes keys and policies to never expire and never update. Use 0
hours for drop and clear policy types.
• Daily at - enter the re-key time using the 24 hour system clock set to the
required local time of the ETPM workstation. The re-key time will translate to
the local times of the ETKMSs and PEPs that might be located in other time
zones.
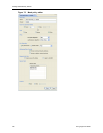
Type Specifies the action applied to packets that match the protocol and networks
included in this policy.
•Drop - drops all packets matching this policy.
•Bypass - passes all packets matching this policy in the clear.
• IPSec - encrypts or decrypts all packets matching this policy.
IPSec Specifies the encryption and authentication algorithms used in an IPSec policy.
Select the encryption algorithm from the Encryption Algorithms list:
•AES - Advanced Encryption Standard (default)
•3DES - a more secure variant of Data Encryption Standard
Select the authentication algorithm from the Authentication Algorithms list:
• HMAC-SHA-1 - Secure Hash Algorithm
• HMAC-MD5 - Message Digest 5
Note: Layer 4 policies require AES and HMAC-SHA-1.
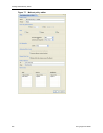
Key Generation Specifies the key generation and distribution mechanism for the PEPs included
in this policy.
• By Network Set - The default ETKMS within each network set generates
and distributes the keys to the PEPs included in those network sets.
• Global ETKMS - A global ETKMS generates the keys and sends them to
the default ETKMSs in each network set for distribution to all of PEPs
included in the policy.
Select the desired ETKMS from the Global ETKMS list.