Intel
®
IXP400 Software
Access-Layer Components: Security (IxCryptoAcc) API
April 2005 IXP400 Software Version 2.0 Programmer’s Guide
104 Document Number: 252539, Revision: 007
2. Use AES-CTR mode to encrypt the payload with counter values 1, 2, 3, …
3. Use AES-CTR mode to encrypt the MIC with counter value 0 (First key stream (S0) from
AES-CTR operation)
The API usage for performing an IPSec-style AES-CCM operation is as follows:
1. Register a crypto context for AES-CBC encryption (cipher context). A crypto context ID (A,
in this example) will be obtained in this operation. Non-in-place operation must be chosen
(useDifferentSrcAndDestMbufs in IxCryptoAccCtx must set to TRUE) to avoid the original
data being overwritten by encrypted data. This crypto context is used only for the purpose of
authentication and generating the MIC.
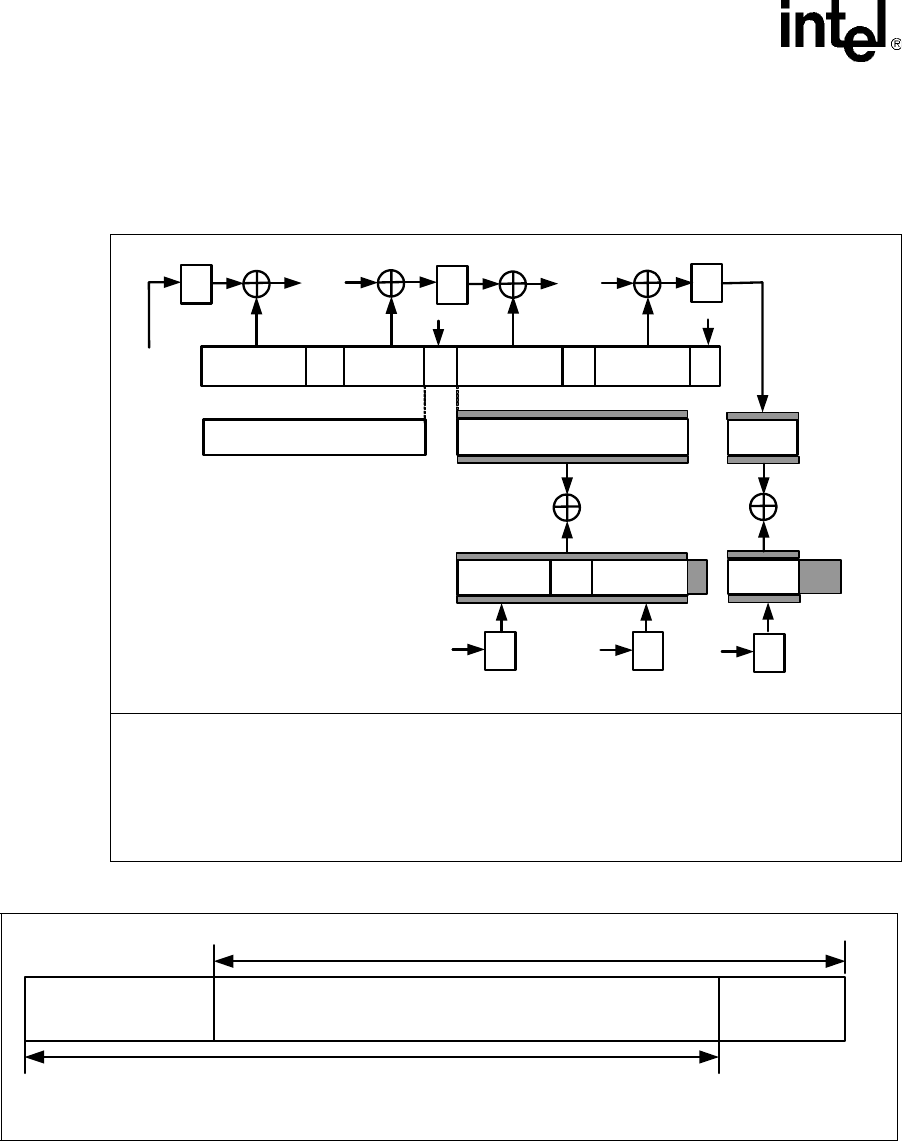
Figure 37. CCM Operation Flow
Legend:
E – Encryption operation
B – Data blocks to be encrypted (data is split into multiple blocks of the size of cipher block length)
S – Key stream generated from AES-CTR encryption
A – Counter blocks for AES-CTR encryption
MIC – Message Integrity Code
Figure 38. CCM Operation on Data Packet
Header
Payload
MI C
E
EE
E
E
E
A
1
... A
m
A
0
...
...
padding
padding
B
1
…B
k
0B
k+1
…B
r
0
S
1
S
m
S
0
...
B
0
B3002-01
Header payload MIC
Encrypted
Authenticated
B3003-0
1


















