Intel
®
IXP400 Software
Access-Layer Components: Security (IxCryptoAcc) API
Programmer’s Guide IXP400 Software Version 2.0 April 2005
Document Number: 252539, Revision: 007 97
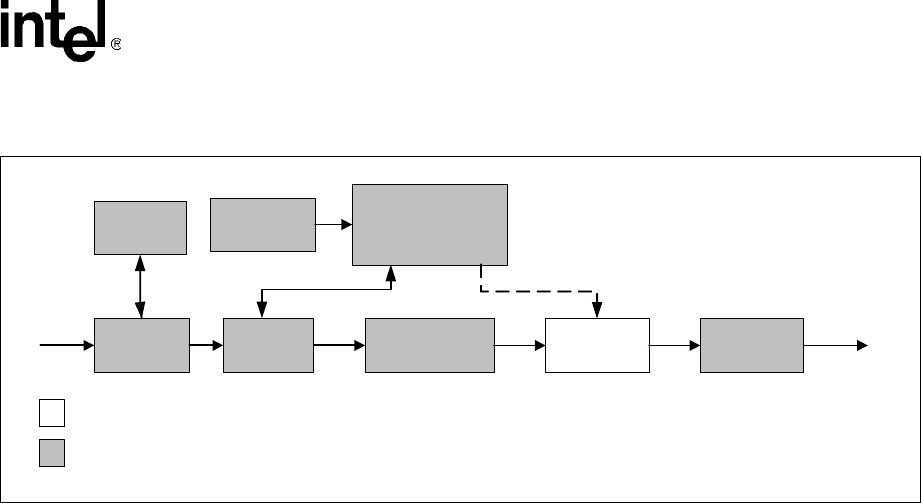
The IPSec protocol stack provides security for the transported packets by encrypting and
authenticating the IP payload. Before an IP packet is sent out to the public network, it is processed
by the IPSec application (the IxCryptoAcc and supporting components, in this scenario) to
encapsulate the IP packet into the ESP or AH packet format.
The information within the SA database that is required for the cryptographic protection is passed
in via the client to the Hardware Accelerator (in the Cryptographic Protection Block). The client
looks up the crypto context policy and SA database to determine the mode of transporting packets,
the IPSec protocol (ESP or AH), etc. The client determines use of the transport or tunnel mode
from the registered security context. The mode is transparent to the hardware accelerator and the
ixCyptoAcc component.
The client processes the IP packet into ESP- or AH-packet format, the IP packet is padded
accordingly (if ESP is chosen), and the IP header mutable fields are handled (if AH). Then, based
on the SA information, the NPE executes cryptographic protection algorithms (encryption and/or
authentication). This is done regardless of whether transport or tunnel mode is used.
The client sends out the protected IP packet after the cryptographic protection is applied. If the IP
packet is too large in size, the client fragments the packet before sending.
Figure 31 shows the relationship of encryption and authentication algorithms within the IPSec
protocol.
Figure 30. IxCryptoAcc, NPE and IPSec Stack Scope
Policy
Lookup
Packet Processing
Cryptographic
Protection
IP
Fragmentation
Crypto Context
Database
Original IP
Packet
IPSec'd
Packet
Hardware Accelerator (NPE) Scope
Client IPSec’s scope
SA Lookup
SA Database
Management
B2313-02
Policy
Database


















