Intel
®
IXP400 Software
Access-Layer Components: Security (IxCryptoAcc) API
Programmer’s Guide IXP400 Software Version 2.0 April 2005
Document Number: 252539, Revision: 007 107
• *pSrcMbuf — a pointer to IX_MBUF, which contains data to be processed. This IX_MBUF
structure is allocated by client. Result of this request will be stored in the same IX_MBUF and
overwritten the original data if UseDifferentSrcAndDestMbufs flag in IxCryptoAccCtx is set
to FALSE (in-place operation). Otherwise, if UseDifferentSrcAndDestMbufs flag is set to
TRUE, the result will be written into destination IX_MBUF (non-in-place operation) and the
original data in this IX_MBUF will remain unchanged.
• *pDestMbuf — Only used if UseDifferentSrcAndDestMbufs is TRUE. This is the buffer
where the result is written to. This IX_MBUF structure is allocated by client. The length of
IX_MBUF must be big enough to hold the result of operation. The result of operation cannot
span into two or more different IX_MBUFs, thus the IX_MBUF supplied must be at least the
length of expected result. The data is written back starting at startOffset in the pDestMbuf.
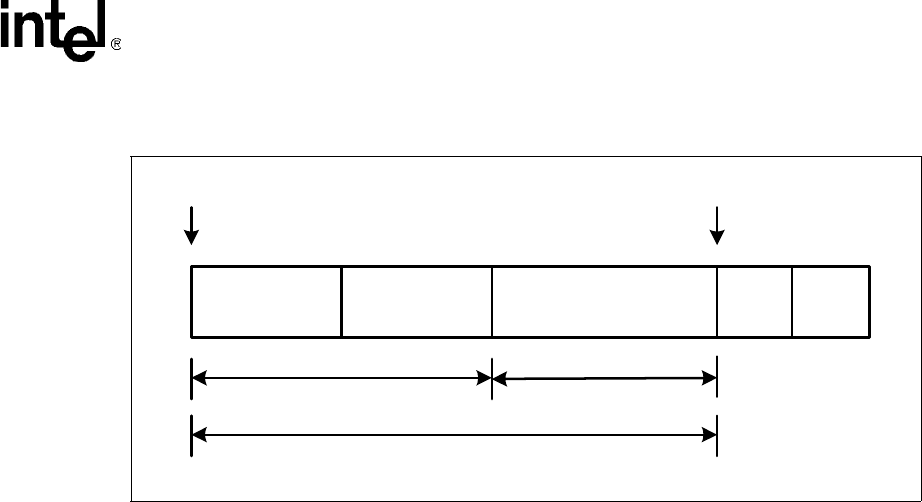
• startOffset — Supplied by the client to indicate the start of the payload to be decrypted/
encrypted or authenticated.
• dataLen — Supplied by the client to indicate the length of the payload to be decrypted/
encrypted in number of bytes.
• icvOffset — Supplied by the client to indicate the start of the ICV (Integrity Check Value)
used for the authentication. This ICV field should not be split across multiple IX_MBUFs in a
chained IX_MBUF.
• *pKey — Pointer to IX_CRYPTO_ACC_ARC4_KEY_128 bytes of per packet ARC4 keys.
This pointer can be NULL if the request is WEP IV gen or verify only.
In the figure above, it is assumed for the sake of simplicity that mData is a contiguous buffer
starting from byte 0 to the end of the FCS.
FCS is not computed or touched by the component.
7.5.2 Hardware Acceleration for WEP Services
The WEP services provided in IxCryptoAcc depend on hardware-based resources for some of the
cryptographic functions. This differs from the model of NPE-based hardware acceleration typically
found in the IXP400 software in that the client software can select to use NPE-based acceleration
or an Intel XScale core-based software engine that both provide equivalent functionality.
Figure 41. WEP Frame with Request Parameters
Frame Header IV Header Frame Body ICV FCS
mData ptr
startOffset
d
a
t
a
L
e
n
icvOffset
i cv ptr
B2919-0
1


















