Intel
®
IXP400 Software
Access-Layer Components: Security (IxCryptoAcc) API
Programmer’s Guide IXP400 Software Version 2.0 April 2005
Document Number: 252539, Revision: 007 105
2. Register another crypto context for AES-CTR encryption (cipher context). A crypto context
ID (B) will also be obtained in this operation. This crypto context is used for payload and MIC
encryption only.
3. After both crypto context registration for both contexts is complete, call the crypto perform
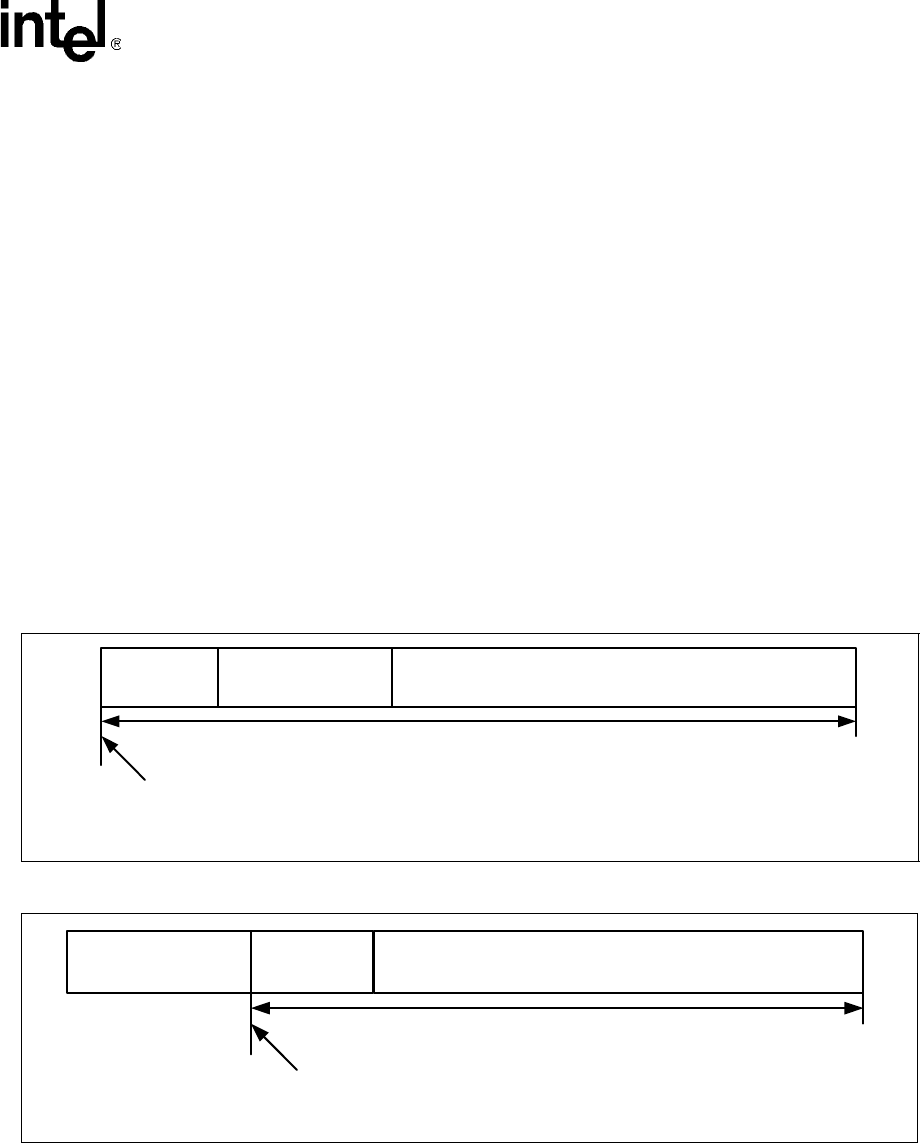
API using context ID A. The IV for this packet is inserted as first block of message in the
packet. The input IV to the crypto perform function is set to zeroes. Crypt start offset and crypt
data length parameters are set to the same values as authentication start offset and
authentication data length, as shown in Figure 39 on page 105. Authentication start offset and
authentication data length can be ignored in the API for this operation, as this is an encryption
operation only. The client should handle all the above-mentioned steps before calling the
crypto perform function.
4. Wait for the operation in step 3 to complete and extract the MIC from the destination
IX_MBUF using the callback function.
5. Append the MIC from step 4 into the IX_MBUF before the payload data.
6. Call the crypto perform function with crypto context ID B. Change the crypt start offset to
point to the start offset of the MIC and change the crypt data length to include the length of
MIC, as shown in Figure 40 on page 105.
7. Wait for operation in step 6 to complete and move the MIC back to its original location in
IX_MBUF. The MIC is now the final authentication data.
Since the data has to be read twice by the NPE, this two-pass mechanism will have slower
throughput rate compared to the other crypto perform operations that combine encryption and
authentication.
Note that memory copying is needed when performing the CCM request on a packet as mentioned
above. Chained IX_MBUFs could be used to avoid excessive memory copying in order to get
better performance. If a single IX_MBUF is used, memory copying is needed to insert MIC from
Figure 39. AES CBC Encryption For MIC
Figure 40. AES CTR Encryption For Payload and MIC
Header Payload
Crypt Data Length
(Authentication Data Length)
Ori ginal IV
Crypt Start Offset
(Authentication Start Offset)
B3004-0
1
Header PayloadMIC
Crypt Start Offset
Crypt Data Length
B3005-0
1


















