Intel
®
IXP400 Software
Access-Layer Components: Security (IxCryptoAcc) API
Programmer’s Guide IXP400 Software Version 2.0 April 2005
Document Number: 252539, Revision: 007 109
1. The proper NPE microcode images must have been downloaded to the NPE and initialized.
Additionally, the IxCryptoAcc API must be properly configured, initialized, and the crypto
context registration procedure must have completed.
At this point, the client must create the IX_MBUFs that will hold the target data and populate
the source IX_MBUF with the data to be operated on. The client must supply the ARC4 key
for the ARC4 algorithm.
2. The client submits the ixCryptoAccNpeWepPerform() or ixCryptoAccXscaleWepPerform()
function, supplying the crypto context ID, pointers to the source and destination buffer, offset
and length of the authentication and crypto data, offset to the integrity check value, and a
pointer to the ARC4 key.
3. IxCryptoAcc will use IxQMgr to place a descriptor for the data into the WEP Request Queue.
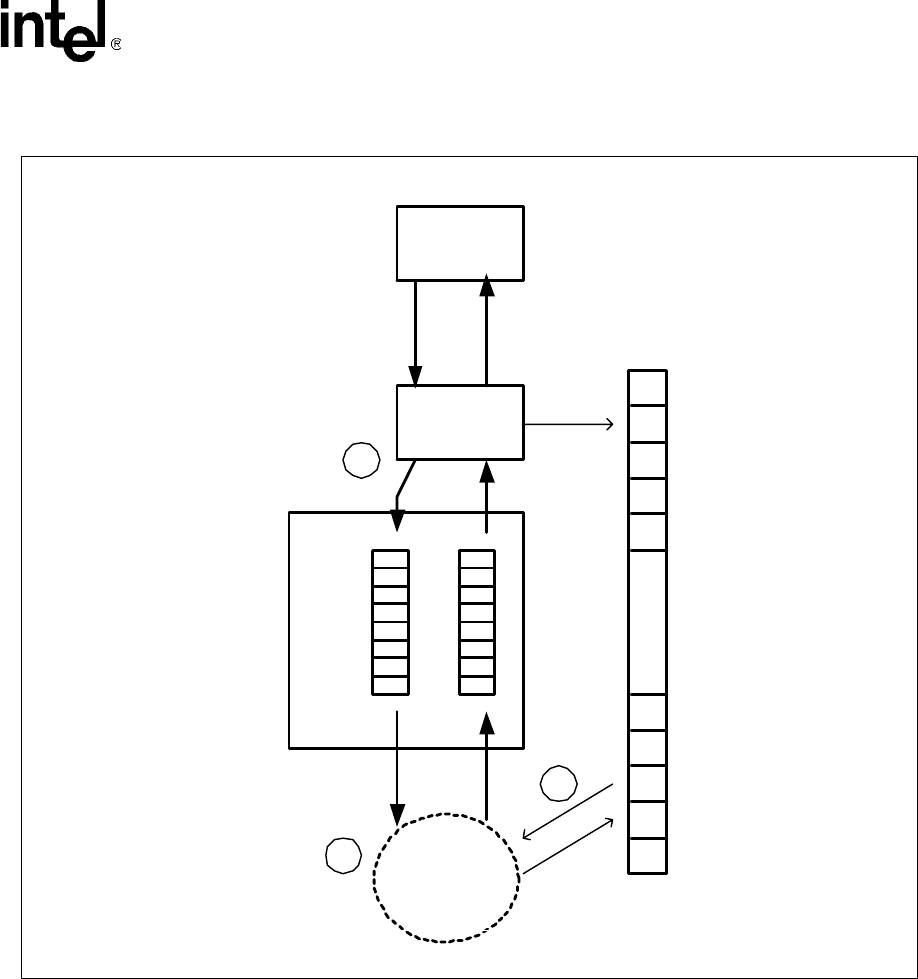
Figure 42. WEP Perform API Call Flow
WEP Client
1. (...NPE init, CryptoAccConfig,
CryptoAccInit, CryptoAccCtxRegister,
etc...)
create data mBufs, IV
2. ixCryptoAcc*WepPerform (cryptoCtxId,
*pSrcMbuf, *pDestMbuf, startOffset,
dataLen, icvOffset, *pKey)
IxQMgr / AQM
NPE - A
or
Intel
®
XSc ale
Core WEP
Engine
6. ixCryptoPerformCompleteCallback
(cryptoContextId, mBuf *, IxCryptoAccStatus)
IxCryptoAcc
WEP Request Queue
WEP Complete Queue
SDRAM
3.
4.
5.
B2920-01


















