DES-7200 Configuration Guide Chapter 1 AAA Configuration
1-3
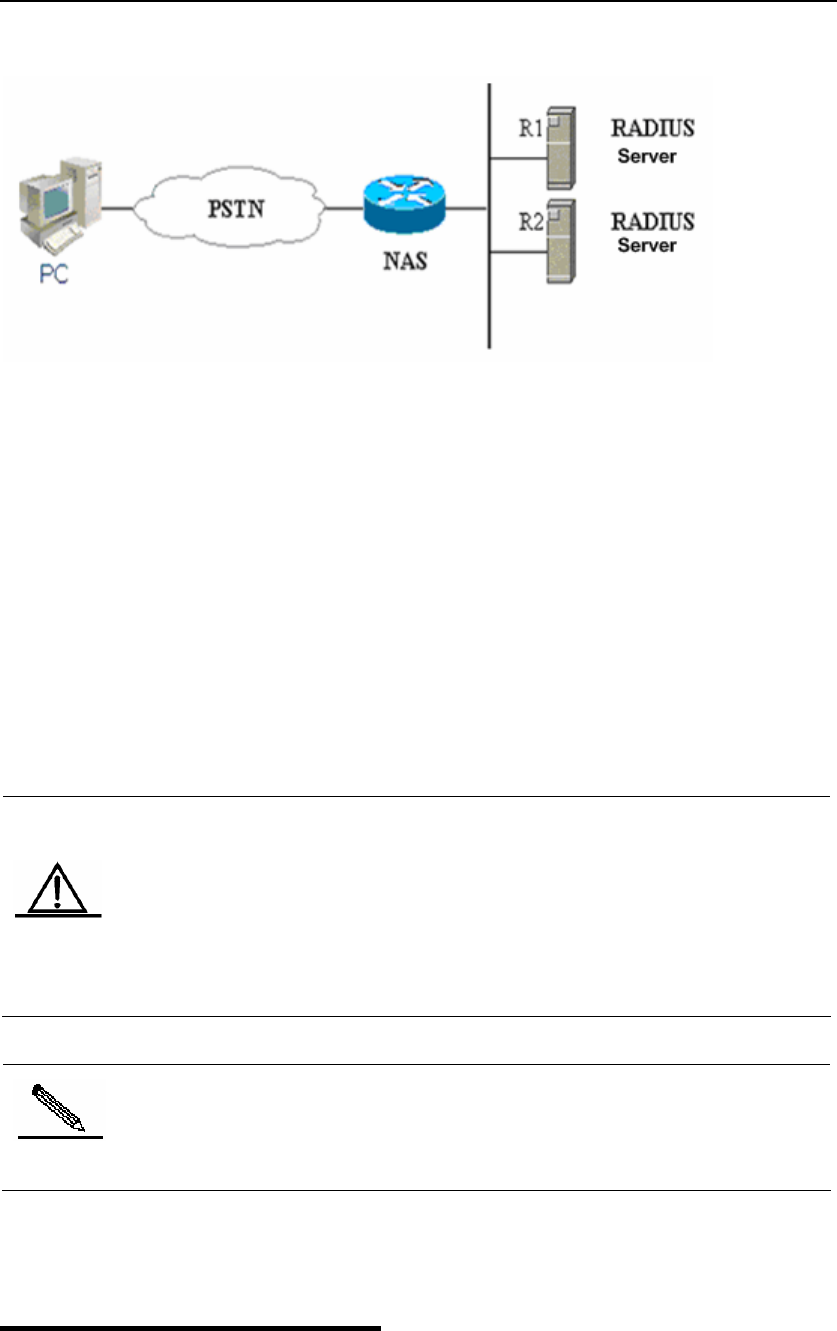
A typical AAA network configuration
The figure above illustrates a typical AAA network configuration, including two security servers:
R1 and R2 are both RADIUS servers.
Supposed the system administrator has defined a method list, R1 is used first to capture the
identity information, then R2, and finally the local username database on the NAS. If a remote
PC user attempts to access the network via dialup, the NAS first queries the authentication
information from R1. If the user passes the authentication on R1, R1 sends a SUCCESS reply
to the NAS, and thus the user's access to the network is allowed. If R1 returns FAIL reply, the
user's access is refused and the disconnected. If R1 has no reply, the NAS regards it as
ERROR and queries authentication information from R2. This process continues for the
remaining methods till the user passes the authentication, is refused or the session is
terminated. If ERROR is returned for all methods, the authentication fails and the user is
disconnected.
Caution
The REJECT response is not the same as the TIMEOUT response. REJECT
means the user fails to comply with the standard in the available authentication
database and does not pass the authentication, thus the access request will be
refused. TIMEOUT means there is no reply from the security server to the
authentication. When an ERROR is detected, the AAA selects the next
authentication method in the method list to continue the authentication process.
Note
In this chapter, take RADIUS for example of the configuration of the related
authentication, authorization and accouting of the AAA security server. For the
TACACS+, refer to TACACS+ Configuration.
1.2 Basic AAA
Configuration Steps
First you shall decide to choose which security solution, evaluate the potential security risks in


















