DES-7200 Configuration Guide Chapter 6 URPF Configuration
6-12
6.4 Typical URPF
configuration example
6.4.1 Example of strict
mode configuration
6.4.1.1 Networking requirements
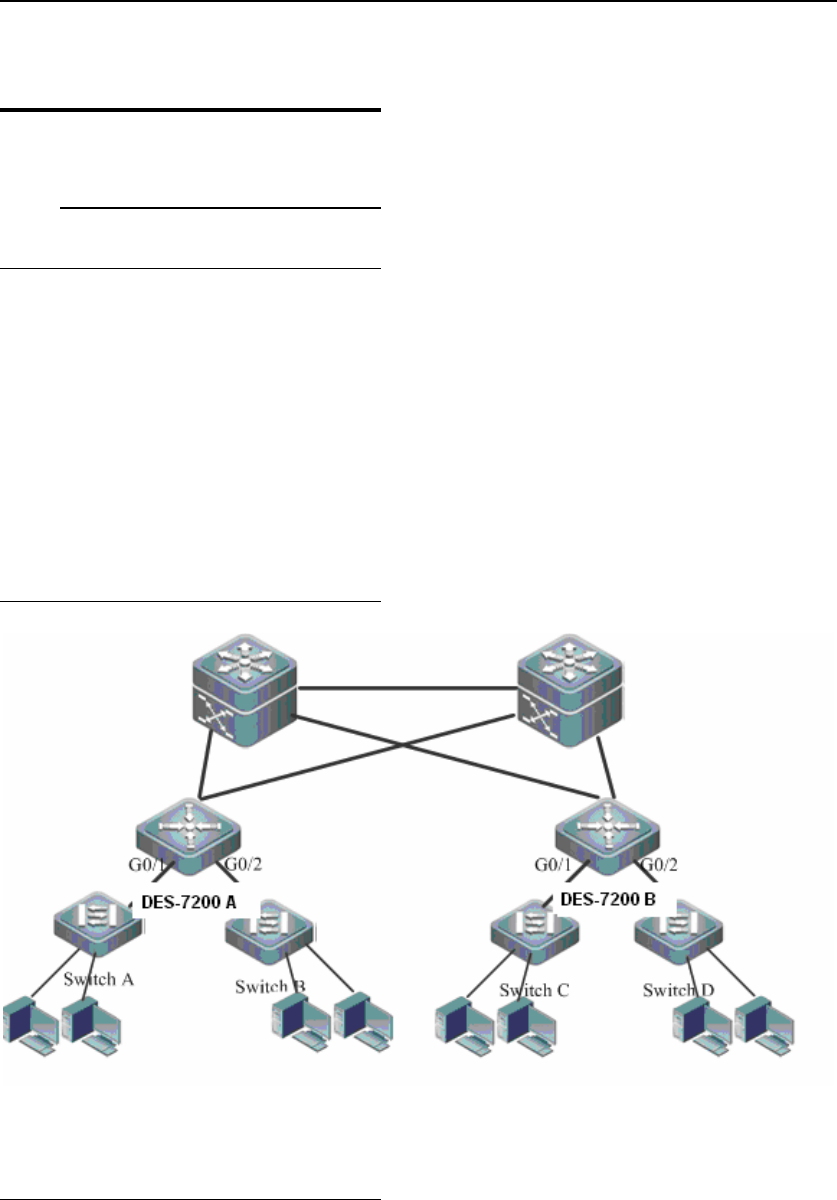
Fig 5 shows an example of typical hierarchical network architecture.
In order to avoid messages with forged source address is transmitted from user PC to the
core-layer network, it is expected that the source address attack messages are isolated in the
access layer or distribution layer, so as to eliminate such invalid data on the distribution-layer
and core-layer network.
By enabling URPF strict mode on the interface linking distribution-layer device and
access-layer device, the aforementioned needs can be satisfied.
6.4.1.2 Network topology
Fig 5 Application of URPF strict mode
6.4.1.3 Configuration steps
As shown in Fig 5, URPF strict mode is enabled on the distribution-layer device: enable URPF
strict mode on device DES-7200 A and device DES-7200 B, as shown below:
# Configurations of device DES-7200-A:
DES-7200# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.


















