DES-7200 Configuration Guide Chapter 11 IP Source Guard Configuration
11-2
the request received from legal client to the server in that trusted network which
allocates and manages addresses.
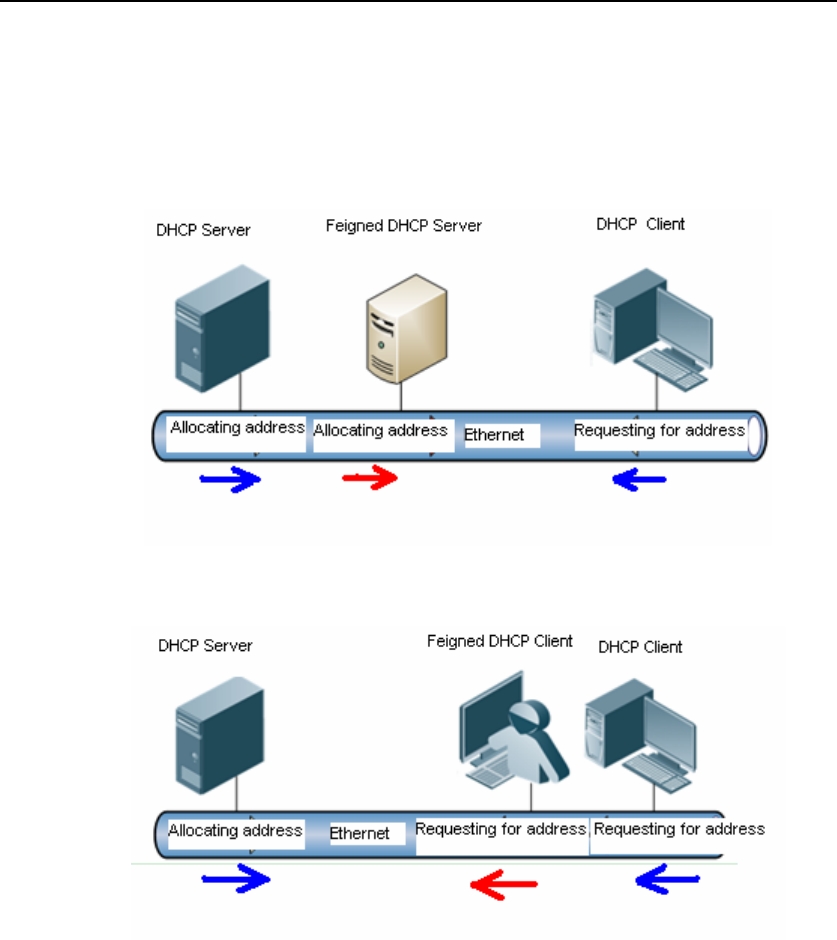
Figure 2 Network with feigned DHCP server
Figure 3 Network with feigned DHCP client attack
Figure 4 Network protected by DHCP Snooping


















