DES-7200 Configuration Guide Chapter 1 AAA Configuration
1-36
1.10 Typical AAA
Configuration Example
1.10.1 Typical AAA
Aplication
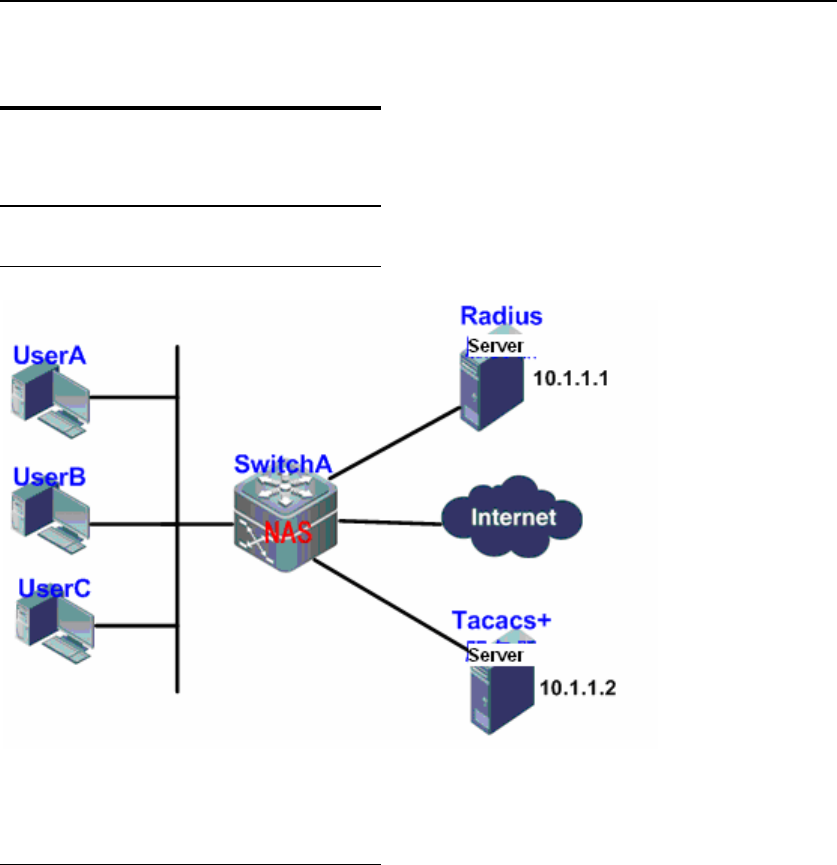
1.10.1.1 Network Topology
Figure 3 Typical AAA Application Topology
1.10.1.2 Network Requirements
For better security management for the SwitchA in the Figure-3, the followings are the network
requirements:
1. The administrators shall have the individual username and password for the convenience of
the account management.
2. The user authentication methods are divided into local authentication and collection
authentication. The method of combining the collection-authentication with the
local-authentication shall be adopted, with the collection-authentication mainly-used and the
local-authentication as backup. In the process of the collection-authentication, the Radius
server authentication shall be passed first, if there is no reply, it will switch to the local
authentication.
3. Different users can be configured to access to the specified network device during the
authentication.
4. User management priority: divide the network management users into the super users and
ordinary users, wherein the super users own the priority of reading and writing while the


















