DES-7200 Configuration Guide Chapter 11 IP Source Guard Configuration
11-3
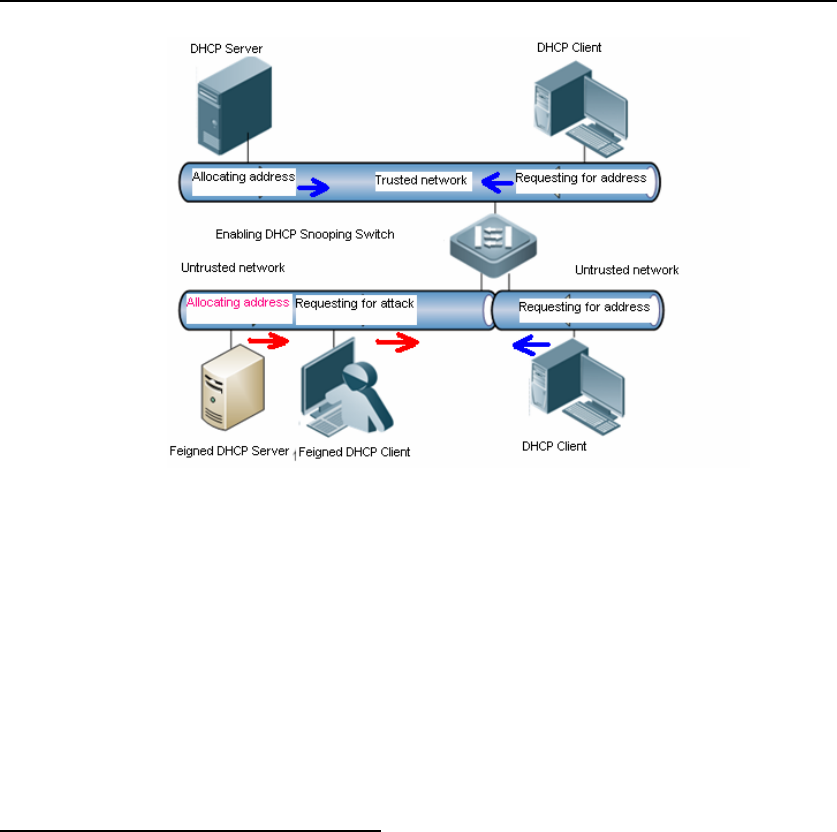
By filtering DHCP packets, DHCP Snooping shields feigned servers and block the
attacks from the clients. However, it cannot control the users assign IP addresses
privately. Those users easily lead to conflict of network addresses and be harm to the
management of network addresses. To prevent the clients from assigning addresses
privately in the DHCP network, enable IP Source Guard on the device connecting the
DHCP server to the DHCP clients. DHCP Snooping-based IP Source Guard
ensures that DHCP clients access network resources properly and block the users
who assign addresses privately to access.
11.1.2 Understanding IP Source
Guard
IP Source Guard maintains a hardware-based IP packet filtering database to filter
packets, guaranteeing that only the users matching the database can access network
resources.
The hardware-based IP packet filtering database is the key for IP Source Guard to
enable efficient security control in DHCP applications. This database is on the basis
of DHCP Snooping database. After IP Source Guard is enabled, the DHCP Snooping
database is synchronized with the hardware-based IP packet filtering database. In
this way, IP Source Guard can strictly filter IP packets from clients on the device with
DHCP Snooping enabled.
By default, once IP Source Guard is enabled on a port, all the IP packets traveling
through the port (except for DHCP packets) will be checked on the port. Only the
users attaining IP addresses through DHCP and the configured static binding users
can access the network.
IP Source Guard supports source MAC- and source IP-based filtering or source
IP-based filtering. In the former case, IP Source Guard will check the source MAC
and source IP addresses of all packets and only allow those packets matching the


















