DES-7200 Configuration Guide Chapter 4 802.1x Configuration
4-2
By using 802.1x, our switches provide Authentication, Authorization, and Accounting (AAA).
Authentication: It is used to determine whether a user has the access, restricting illegal
users.
Authorization: It authorizes the services available to users, controlling the rights of valid
users.
Accounting: It records users' use of network resources, providing the supporting data for
charging.
The 802.1x is described in the following aspects as below:
Device Roles
Authentication Initiation and Packet Interaction During Authentication
States of Authorized Users and Unauthorized Users
Topologies of Typical Applications
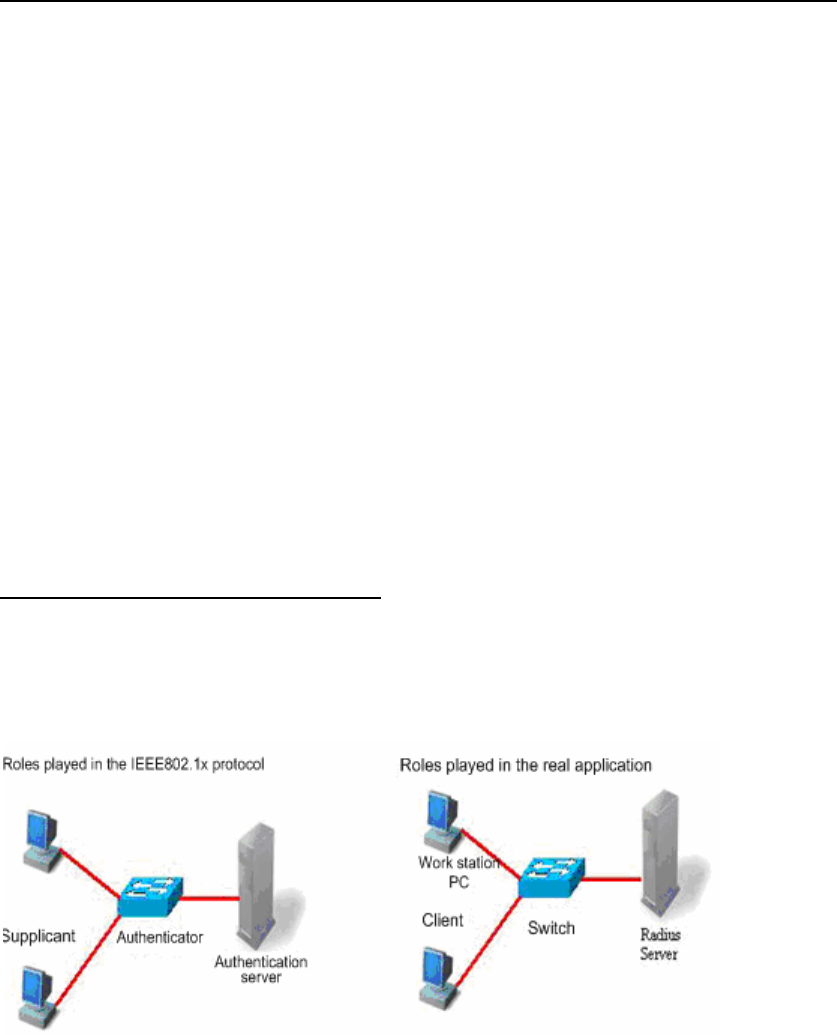
4.1.1 Device Roles
In the IEEE802.1x standard, there are three roles: supplicant, authenticator, and
authentication server. In practice, they are the Client, network access server (NAS) and
Radius-Server.
Supplicant:
The supplicant is a role played by the end user, usually a PC. It requests for the access to
network services and acknowledges the request packets from the authenticator. The
supplicant must run the IEEE 802.1x client. Currently, the most popular one is the IEEE802.1x
client carried by Windows XP. In addition, we have also launched the STAR Supplicant
software compliant of this standard.
Authenticator:
The authenticator is usually an access device like the switch. The responsibility of the device
is to control the connection status between client and the network according to the current


















